Automate Azure API Management: Backup and Restore

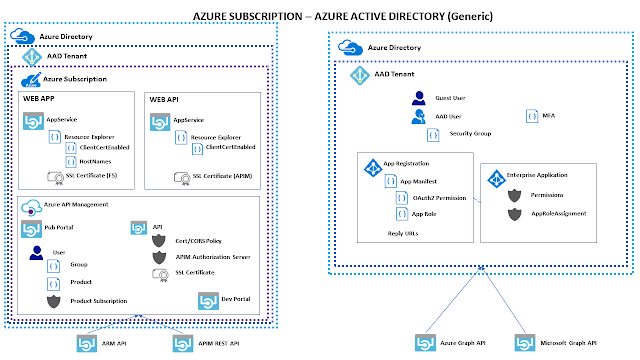
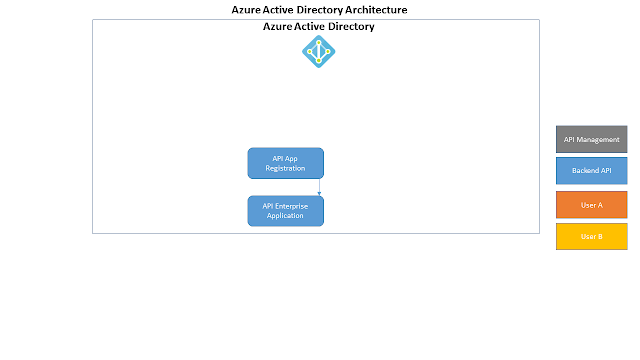
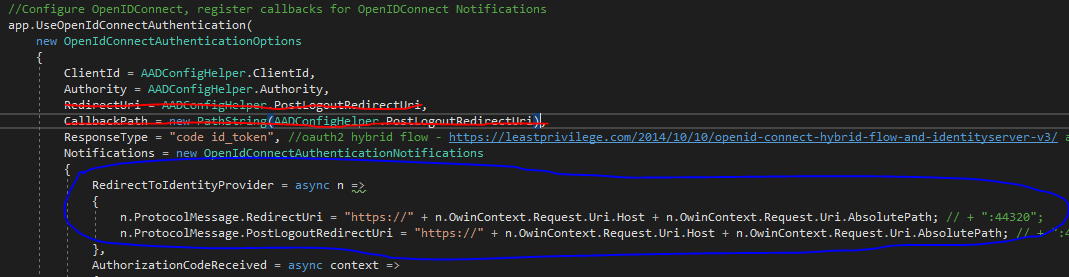
Once you setup the service in Azure and add all your APIs, you should make sure you have a good Backup strategy in place, in case things go wrong. If you do regularly backup the service, then you can also use those backups for a couple of purposes: you can for example deploy more than one instance and put a Traffic Manager in front of them, in order to handle geographical distribution . But you can also restore a specific backup to a different Subscription , and create a separate environment, as per the DTAP street . Azure API Managemen t provides a REST API that you can use to automate things; unfortunately that works for most features and activities, but not for backing up and restoring the whole service. For this you need to use the good "old" ARM , which also provides a REST API with specififc API Management operations. By reading the article above, you might think that this is as easy as getting a token , backing up and restoring the service... Well,